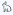Light
Mitigate the Pitch Black attack (the simulation works)
Mo, 02/08/2016 - 11:37 — DraketoI fixed a small bug in the simulator of thesnark. With that, the simulator shows that the defense against the Pitch Black Attack works: A small number of attackers can no longer kill parts of the keyspace and can also no longer make certain parts of the keyspace inaccessible.
Attackers can still limit the convergence of the network towards a reproduction of the small world network, but since we know that Opennet works quite well with 30% backoff, this limited convergence should suffice for efficient routing.
- Login to post comments
- Weiterlesen
Python chooses Github, therefore I’m releasing the py2guile PDF for free
Mi, 01/06/2016 - 23:54 — DraketoPython is the first language I loved. I dreamt in Python, I planned in Python, I thought I would never need anything else.
Download “Python to Guile” (pdf)
You can read more about this on the Mercurial mailing list.
- Free: html | pdf
preview edition
(complete)
Yes, this means that with Guile I will contribute to a language developed via Git, but it won’t be using a proprietary platform.
- Login to post comments
- Weiterlesen
Conversion factor from ppmv CO₂ to Gt C
Fr, 11/06/2015 - 12:44 — DraketoI just spent half an hour on finding the references for this, so I can spend 5 minutes providing it for others on the web.
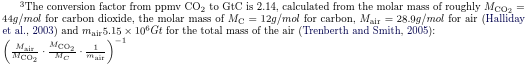
- Login to post comments
- Weiterlesen
Translating a lookup-dictionary to bash: Much simpler than I thought
Mi, 10/21/2015 - 18:18 — DraketoI wanted to name Transcom Regions in my plots by passing their names to the command-line tool, but I only had their region-number and a lookup dictionary in Python. To avoid tampering with the tool, I needed to translate the dictionary to a bash function, and thanks to the case statement it was much simpler than I had expected.
This is the original dictionary:
- Login to post comments
- Weiterlesen
GNU Guix in 5 minutes
Mo, 10/19/2015 - 16:48 — DraketoSo you get excited when you hear about surviving a power-outage during updates without a hitch and you want to give Guix a try — but woes, you only have 5 minutes of time?
Fear not, that’s enough to get it up and running — all the way to per-user environments and package install as non-priviledged user!
The instructions here are from the official docs, specialized for a GNU Linux host and cut to what I need in a working system.
as user:
$ cd /tmp
$ wget ftp://alpha.gnu.org/gnu/guix/guix-binary-0.8.3.x86_64-linux.tar.xz
- Login to post comments
- Weiterlesen
Gratis py2guile from Freenet
Sa, 10/17/2015 - 12:04 — Draketopy2guile is a book I wrote about Python and Guile Scheme. It’s selling at 14.95 € for the printed softcover.
To fight the new german data retention laws, you can get the ebook gratis: Just install Freenet, then the following links work:
Escape total surveillance and get an ebook about the official GNU extension language for free today!
- Login to post comments
BY-SA and GPL: creativecommons closed the chasm in the sharealike/copyleft community
Do, 10/08/2015 - 18:03 — DraketoThis is the biggest news item for free culture and free software in the past 5 years: The creativecommons attribution sharealike license is now one-way compatible to the GPL — see the message from creativecommons and from the Free Software Foundation.
- Blender rigs under cc by-sa which use libraries under GPL are safe against suing, even if a Blender code contributor goes crazy,
- 3D models like the self replicating 3D printer RepRap and libre hardware designs under cc by-sa and GPL can be combined,
- GPL-compatible Free Software can utilize all content from the Wikipedia and
- On the personal side: we can merge art from Ryzom and Battle for Wesnoth and use both in the Pirate Party RPG.
Some license compatibility legalese might sound small, but the impact of this is hard to overestimate.
- Login to post comments
- Weiterlesen
Going from Python to Guile Scheme - a natural progression
Do, 10/01/2015 - 21:42 — DraketoPython is the first language I loved. I dreamt in Python, I planned in Python, I thought I would never need anything else.
- Free: html | pdf
- Softcover: 14.95 €
with pdf, epub, mobi
- Source: download
free licensed under GPL
- Login to post comments
- Weiterlesen
Australia gets mandatory data retention
Mo, 09/21/2015 - 08:32 — DraketoAustralia gets mandatory data retention — with unchecked access by roughly any local or federal police agency and “Any other agency the Attorney General publicly declares”. (So much for separation of powers)
And they can use that in court.
→ » Australia: Now is the time to go dark « ←
Dear Australians: This is what we have been talking about the past 10 years. The tech for confidential communication might still be cumbersome to use, but you now need it.
If you want to use Freenet for that, I’ll gladly help you set it up.
- Login to post comments
- Weiterlesen
IPCC bibtex entries
Di, 09/15/2015 - 09:49 — DraketoI repeatedly stumbled over needing bibtex entries for the IPCC reports. So I guess, others might stumble over that, too. Here I share my bibtex entries for some parts of the IPCC reports.1
IPCC 1990 WG1 (physical science basis)
@BOOK{IPCC1990Science,
title = {Climate Change 1990 The Science of Climate Change},
publisher = {The Intergovernmental Panel on Climate Change},
year = {1996},
editor = {J.T. Houghton and G.J. Jenkins and J.J. Ephraums},
author = {IPCC Working Group I}
}
-
In IPCC 2013 WG1 they finally provide bibtex in their zip of references, but without item headers — you can’t use these directly. ↩
- Login to post comments
- Weiterlesen
Freenet as backing store for sites on the clearnet (in use today)
Mo, 09/14/2015 - 16:42 — DraketoChris Double (bluishcoder) changed his main website to be served directly from Freenet:
Thanks to this, the same article is now available from my inproxy.
And, naturally, from Freenet:
USK@1ORdIvjL2H1bZblJcP8hu2LjjKtVB-rVzp8mLty~5N4,8hL85otZBbq0geDsSKkBK4sKESL2SrNVecFZz9NxGVQ,AQACAAE/bluishcoder/20/2015/09/14/using-freenet-for-static-websites.html
- Login to post comments
- Weiterlesen
Information challenges for scientific publishing
Fr, 08/28/2015 - 20:54 — DraketoOn 2015-08-27, Researchers from the Reproducibility Project: Psychology reported that in 100 reproduction studies, only “47% of original effect sizes were in the 95% confidence interval of the replication effect size” (RPP SCIENCE 2015, an overview of the results is available in Scientific American; in german from DLF Forschung Aktuell).
I take this worrying result as cue to describe current challenges to scientific publishing and measures to address them — including reproduction experiments, and what to do if they contest previously published and referenced work.
Scientific publishing has come a long way since its beginning, and its principles have allowed it to scale up from a few hundred active scientists worldwide to conferences with tens of thousands of people for a given topic. But in the last few years it hit its limits. It becomes harder each year to keep up with the amount of new papers being published and even scientists from similar fields repeatedly reinvent the same methods. To scale further and to continue to connect the scientific community, it must adapt to make it easier to get an understanding of the current state of science and keep up to date with new findings.
To grow from these challenges, scientific publishing needs to
- make it easier to get and stay up to date with several fields,
- foster reproducible research,
- add incentives for reproduction studies,
- introduce propagating corrections and
- reduce the pressure to publish.
- Login to post comments
- Weiterlesen
Freenet Communication Primitives: Part 2, Service Discovery and Communication
Do, 08/20/2015 - 19:42 — DraketoBasic building blocks for communication in Freenet.
This is a guide to using Freenet as backend for communication solutions - suitable for anything from filesharing over chat up to decentrally hosted game content like level-data. It uses the Python interface to Freenet for its examples.
This guide consists of several installments: Part 1 is about exchanging data, Part 2 is about confidential communication and finding people and services without drowning in spam and Part 3 ties it all together by harnessing existing plugins which already include all the hard work which distinguishes a quick hack from a real-world system (this is currently a work in progress, implemented in babcom_cli which provides real-world usable functionality).
Note: You need the current release of pyFreenet for the examples in this article (0.3.2). Get it from PyPI:
# with setuptools easy_install --user --egg pyFreenet==0.4.0 # or pip pip install --user --egg pyFreenet==0.4.0
This is part 2: Service Discovery and Communication. It shows how to find new people, build secure communication channels and create community forums. Back when I contributed to Gnutella, this was the holy grail of many p2p researchers (I still remember the service discovery papers). Here we’ll build it in 300 lines of Python.
Welcome to Freenet, where no one can watch you read!
- Login to post comments
- Weiterlesen
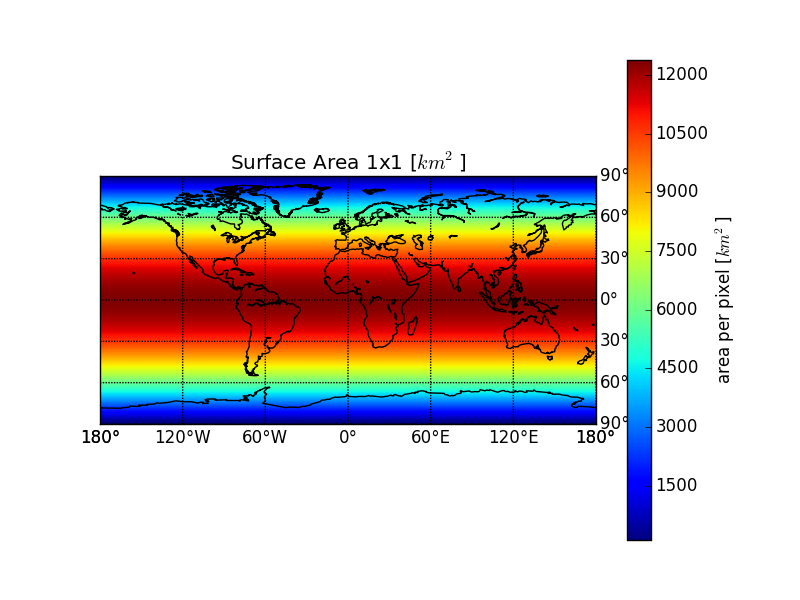
Surface Area of regions on an ellipsoid Earth
Mo, 08/03/2015 - 04:57 — DraketoCalculating the area of arbitrary regions on the Earth approximated as an ellipsoid. I needed this for conversion between the output of different models.
It’s calculated in Emacs Lisp, which showed me that for somewhat complex mathematical tasks Lisp syntax isn’t only unproblematic, but actually helps avoiding mistakes. And full unicode support is great for implementing algorithms with ω, λ and φ.
- Login to post comments
- Weiterlesen
My server was breached - sorry for the downtime
Di, 07/21/2015 - 16:42 — DraketoAfter 4 weeks of downtime my sites are online again.
- Draketo's blog
- Login to post comments
- Weiterlesen
Freenet Communication Primitives: Part 1, Files and Sites
Sa, 07/18/2015 - 18:46 — DraketoBasic building blocks for communication in Freenet.
This is a guide to using Freenet as backend for communication solutions - suitable for anything from filesharing over chat up to decentrally hosted game content like level-data. It uses the Python interface to Freenet for its examples.
This guide consists of several installments: Part 1 (this text) is about exchanging data, Part 2 is about confidential communication and finding people and services without drowning in spam and Part 3 ties it all together by harnessing existing plugins which already include all the hard work which distinguishes a quick hack from a real-world system. Happy Hacking and welcome to Freenet, the forgotten cypherpunk paradise where no one can watch you read!
- Login to post comments
- Weiterlesen
concise commit messages
Mi, 06/10/2015 - 00:26 — DraketoWritten in the discussion about a pull request for Freenet.
When I look up a commit, I’m not searching for prose. I’m searching for short snippets of information I need. If they are long-winded explanations, I am unlikely to even read them.
To understand this, please imagine coming back home, getting off the bike and taking 15 minutes to look at the most recent pull-request.
- Login to post comments
- Weiterlesen
Hitchhikers Guide on Towels - Read from Space
Di, 05/26/2015 - 05:42 — DraketoSamantha Cristoforetti reads the Hitchhikers Guide to the Galaxy on the International Space Station
This is the world we live in: The Hitchhikers Guide read from Space.
If you don’t get goosebumps just thinking about it, envision it again: The old visions are becoming real step by step, and now those who actually venture in space read the works of visionaries from their temporary home beyond the atmosphere.
New traditions form from a reality which still seems
- Login to post comments
- Weiterlesen
Secure communication with GnuPG and E-Mail
So, 05/24/2015 - 22:06 — DraketoHow E-Mail with GnuPG could hide when you talk, where you talk from and what you talk about.
or in technical terms:
E-Mail with perfect forward security, hidden subject and masked date using GnuPG and better frontends.
Update 2018: Some of these ideas are becoming real and widespread now with pΞp (pretty-easy-privacy) and the autocrypt-standard.
If you regularly read my articles, you’ll know that I’m a proponent of connecting over Freenet to regain confidential and pseudonymous communication.
Here I want to show how it would be possible to use E-Mail with GnuPG to get close to the confidentiality of Freenet friend-to-friend communication, because we have the tech (among the most heavily scrutinized and well-tested technology we use today) and we have the infrastructure. All it requires are more intelligent E-Mail clients. Better UI which makes the right thing easy.
Table of Contents
- Login to post comments
- Weiterlesen
Real Life Infocalypse
So, 05/17/2015 - 17:02 — DraketoIn this guide I show by example how you can use the Infocalypse plugin for distributed development without central point of failure or reliance on unfree tools.12
If you think “I have no idea what this tool is for”: Infocalypse gives you fully decentralized Github with real anonymity, using only free software.
# freenet -> local hg clone freenet://ArneBab/life-repo # local -> freenet hg clone life-repo real-life hg clone real-life freenet://ArneBab/real-life # send pull request cd real-life hg fn-pull-request --wot ArneBab/life-repo (enter message) # check for pull-requests cd ../life-repo sleep 1800 # (wait for confidential delivery) hg fn-check-notifications --wot ArneBab
If you like this, please don’t only click like or +1, but share it with everyone who could be interested. The one who knows best how to reach your friends is you — and that’s how it should be.
Update 2024: Infocalypse is still recovering from Python 3 breakage. Most of it works again, but there may be rough edges left. Contributions to fix these are very welcome: hg.sr.ht/~arnebab/infocalypse or github.com/hyphanet/infocalypse.
-
This guide shows the convenient way of working which has a higher barrier of entry. It uses WoT Pseudonyms to allow you to insert repositories by Pseudonym and repository name. If you can cope with inserting by private key and sending pull-requests manually, you can use it without the WoT, too, which reduces the setup effort quite a bit. Just skip the setup of the Web of Trust and Freemail and plugins. You can then clone the life repo via
hg clone freenet://USK@6~ZDYdvAgMoUfG6M5Kwi7SQqyS-gTcyFeaNN1Pf3FvY,OSOT4OEeg4xyYnwcGECZUX6~lnmYrZsz05Km7G7bvOQ,AQACAAE/life-repo.R1/4 life-repo. Seehg fn-genkeyandhg help infocalypsefor details. ↩ -
Infocalypse shows one of many really interesting possibilities offered by Freenet. To get a feeling of how much more is possible, have a look at The Forgotten Cryptopunk Paradise. ↩
- Login to post comments
- Weiterlesen
Strong Kerrigan
Di, 05/05/2015 - 21:29 — Draketo→ New Link: draketo.de/kreatives/strong-kerrigan ←
When you win Starcraft 2 Heart of the Swarm in brutal difficulty without losing Kerrigan even once, you get an ending with a truly strong Kerrigan.234
Clearly you are my greatest failure. Now at long last, you will die.
Again Mengsk activates the Xel'Naga artifact. As the lightning from the artifact tears at her flesh and cracks every part of her body, Kerrigan rasps an answer:
-
The epub icon was created by the Oxygen Team (kde.org) and is licensed under the GNU LGPL. ↩
-
This is what I’d have wished to see. But it is just a fantasy, not the actual ending. ↩
-
All characters in this story belong to Blizzard. I also published this story in the Starcraft forums. ↩
-
The one thing I resent about Kerrigan in Starcraft 2 is that they made her weak.
In SC1 Kerrigan embraced and ruled the swarm. She started as strong terran, never to let anyone talk down to her, never afraid to say what she wanted. Then she got infested, and she prevailed over the infestation, becoming the queen of blades, ruling the Zerg instead of being ruled by the Overmind.
In the cutscenes of SC2 she’s a helpless wreck, ever reliant upon the help of others and exposed as a tool of the overmind to free the swarm from Amon.
It feels as if someone wrote the story to deconstruct the legend of the queen of blades. The in-game story seems much better, though: it’s mainly the cinematic cutscenes that make her weak. Including the last one — and that last one is what I set out to fix in this text. ↩
- Login to post comments
- Weiterlesen
power and deception
Mo, 04/20/2015 - 19:13 — DraketoA religious leader is nothing more than a media-star who managed to convince people that the tale, in which he or she is special, is actually true.
Just like aristocrats managed to convince people that what their ancestors did gives them the right to control the lives of other people.
And like the rich convince people that money gives them the right to control a larger part of the world than others.
- Login to post comments
Simple daemon with start-stop-daemon and runit
Mi, 04/15/2015 - 07:08 — DraketoCreating a daemon with almost zero effort.
Table of Contents
- Login to post comments
- Weiterlesen
Freenet protects your DickPic!
Mi, 04/08/2015 - 20:26 — DraketoAfraid that the NSA could steal your DickPic? Freenet to the rescue!
- Install Freenet
- Connect to your friends
- Share your DickPic (or anything else you want to keep private)
- Login to post comments
- Weiterlesen
My Top 20 most popular articles as of 2015
Mi, 04/01/2015 - 11:37 — DraketoI asked myself: Are the most popular articles on my site the ones I like best?
- Login to post comments
- Weiterlesen
Morning has broken
Di, 03/24/2015 - 07:04 — DraketoMorning has broken
beyond repairthe words are spoken
now do you dareto absolve of the error made
or will you die in your own shade?
- Login to post comments
Freenet / Hyphanet: The forgotten cypherpunk paradise
So, 02/01/2015 - 16:30 — DraketoA long time ago in a chatroom far away, select groups of crypto-anarchists gathered to discuss the death of privacy since the NSA could spy on all communications with ease. Among those who proposed technical solutions was a student who later published the widely regarded first paper on Freenet: A decentralized anonymous datastore which was meant to be a cypherpunk paradise: true censorship resistance, no central authority and long lifetime only for information which people were actually interested in.
Many years passed, two towers fell, the empire expanded its hunt for rebels all over the globe, and now, as the empire’s grip has become so horrid that even the most loyal servants of the emperors turn against them and expose their dark secrets to the masses, Freenet is still moving forward. Lost to the eye of the public, Freenet shaped and reshaped itself - all the while maintaining its focus to provide true freedom of the press in the internet.
- Login to post comments
- Weiterlesen
3 steps to destroy Bitcoin for anonymous usage
Do, 01/29/2015 - 08:05 — DraketoBitcoin is often treated as a haven for black market buyers and people who want to avoid illegitimate laws. However 3 simple steps would suffice to mostly obliterate Bitcoin for black market usage of ordinary users.
Breaking Bitcoin
Three steps to break Bitcoin for small scale anonymous usage:
- Login to post comments
- Weiterlesen